Contact forms are not boring
If you can hijack it and scam people

Contact forms look boring.
Until it starts scamming people as your company.
Here are the most common 3 types of issues I see and exploit:
- SMTP injection
- HTML injection
- Client-side parameters in HTTP request
Real world case 1 (SMTP injection):
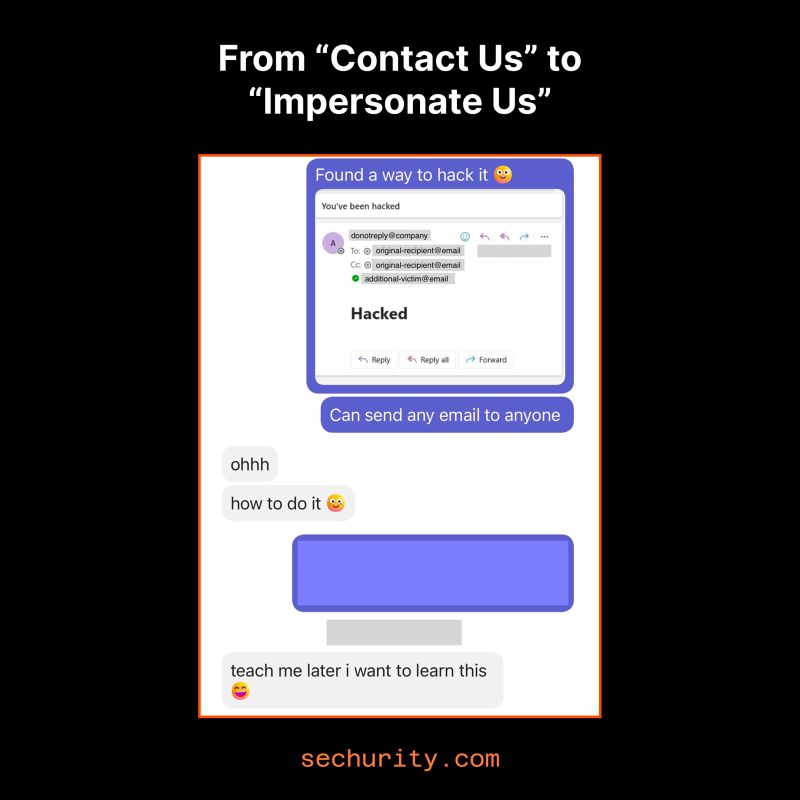
- I appended
\r\ns to my email address when submitting the "Contact Us" form. The acknowledge email turns out to be empty. - Rewrote the entire email and added extra recipients
Real world case 2 (HTML injection):
- Some content seems rendered as HTML judging by the acknowledgement email
- Hiding everything else except my spam message
</p><style>p{display:none;}</style><span>This is now the only thing that shows up.</span><p>
Real world case 3 (Client side parameters and SMTP injection):
- The "Subject" field was in the client HTTP request when submitting the form
- Changing it and adding
\r\ns led to new subject and empty body in the acknowledgement email - Rewrote the entire email and added recipients
Neglecting this can ruin a company's reputation.
Do you really want to be famous for sending out phishing emails to your customers?
So don’t skip the “boring” stuff.
And make sure you ask for/provide access to test it.
References:
SMTP Injection
HTML Injection
Contact forms look boring. | William Chu
Contact forms look boring. Until it starts scamming people as your company.
Here are the most common 3 types of issues I see and exploit: 1. SMTP injection
2. HTML injection
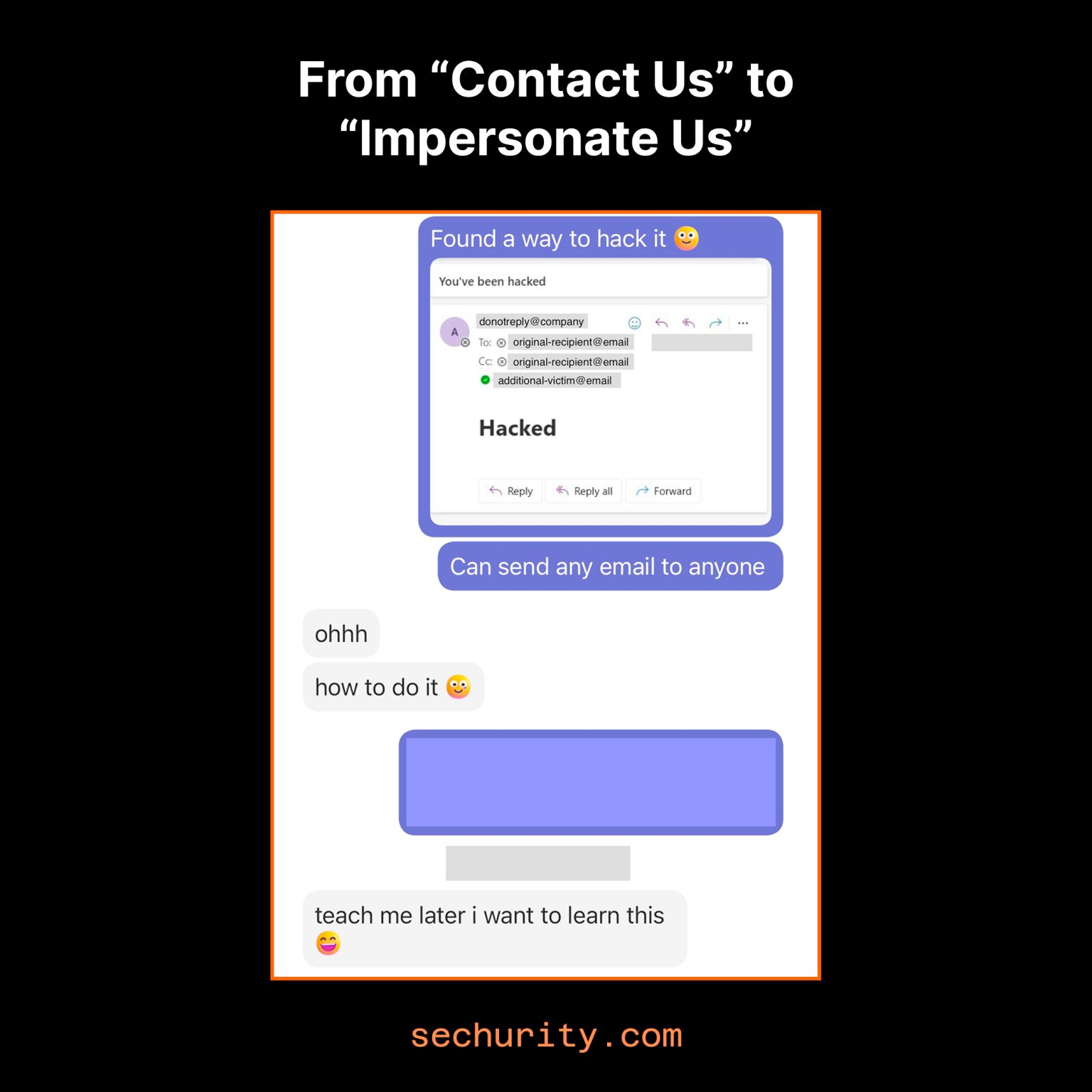
3. Client-side parameters in HTTP request Real world case 1 (SMTP injection):
- I appended`\r\n`s to my email address when submitting the “Contact Us” form. The acknowledge email turns out to be empty. - Rewrote the entire email and added extra recipients Real world case 2 (HTML injection):
- Some content seems rendered as HTML judging by the acknowledgement email
- Hiding everything else except my spam message `</p><style>p{display:none;}</style><span>This is now the only thing that shows up.</span><p>` [2] Real world case 3 (Client side parameters and SMTP injection):
- The “Subject” field was in the client HTTP request when submitting the form
- Changing it and adding `\r\n`s led to new subject and empty body in the acknowledgement email
- Rewrote the entire email and added recipients Neglecting this can ruin a company’s reputation.
Do you really want to be famous for sending out phishing emails to your customers? So don’t skip the “boring” stuff.
And make sure you ask for/provide access to test it. References:
[1] SMTP Injection: https://lnkd.in/gfe4s6wz
[2] HTML Injection: https://lnkd.in/g3BCCgwG